What's Your Back Up Strategy?
Here is the irony of the situation. It was inevitable that it would happen one day; that I would be caught out on the very thing I always preach to my clients. In two words: data backup ... Back up in the sky, Clouds part to reveal the sun, A new day begins This story relates only to my personal data, as I had not got around to properly setting up the backup. I did not have sufficient storage in my generic data centre cloud backup account to store the data that was on my handset, including photographs that I had for the past few years. For only the second time since I have had a mobile phone | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Would you like to know more? |
Did you know, you can negotiate an all-encompassing contract to cover MDM, email security and anti-virus for a single discounted price? Give me a call on |
Share the blog love ... | |||||||||||||||||||||||
#DataBackup #PreachToClients #IronyOfSituation #InevitableHappening #CaughtOut |
About Pritesh Ganatra ... | ||
|
More blog posts for you to enjoy ... | ||
 | Are AI tools disruptive to the human psyche in modern life? Are AI tools disruptive in ways people don't notice until things feel off? This post looks at why younger adults ask AI for life advice, where the risks sit, and how families and firms can respond without panic. It's a pragma... | |
 | What Is The Most Important Part Of Your Business Network? The final words from a recent blog post led me to determine a business network's common point of failure. We're heading into the VoIP era and plunging feet-first into having the traditional PSTN/ISDN networks disconnected for... | |
 | Fraud, Fraud, Fraud! What's The Cost To Your Business? Did you know that small and medium-sized enterprises (SMEs) account for 99.9% of the businesses in the UK? At the start of 2023, there were estimated to be 5.6 million private-sector businesses ...... | |
 | About The Security Of Your Core Business Network The roots of technology, especially in the telecommunications industry, go back to 1837 with the introduction of the Morse code telegraph over copper wires. Prior to that, a written message would need to be handed to a horsem... | |
 | Why you should only use AI as a research tool, not the final word Use AI as a research tool to spark ideas and speed up reading. Then verify, compare sources, and keep judgment yours. It's guidance, not gospel ...... | |
 | Building resilient networks: power requirements in the mobile era I'm exploring how power requirements in the mobile era reshape sustainability, resilience, and network planning. Can we reuse kit, design for repair, and cut waste while still meeting rising demand? It's a practical, optimist... | |
 | Is digital money about to go mainstream in 2026? Digital money is edging closer to everyday life, with regulators, banks and central banks aligning. This post looks at what might click into place in 2026, from tokenised payments to a UK digital pound. It's not guaranteed, b... | |
 | Datacentres Demand Power and Water: How Will AI Affect Our Resources? As the ascent of datacentres keeps accelerating, driven by advancements in generative AI and quantum processors, the demands for electricity and water are growing alarmingly. This surge not only strains resources, but also ha... | |
Other bloggers you may like ... | ||
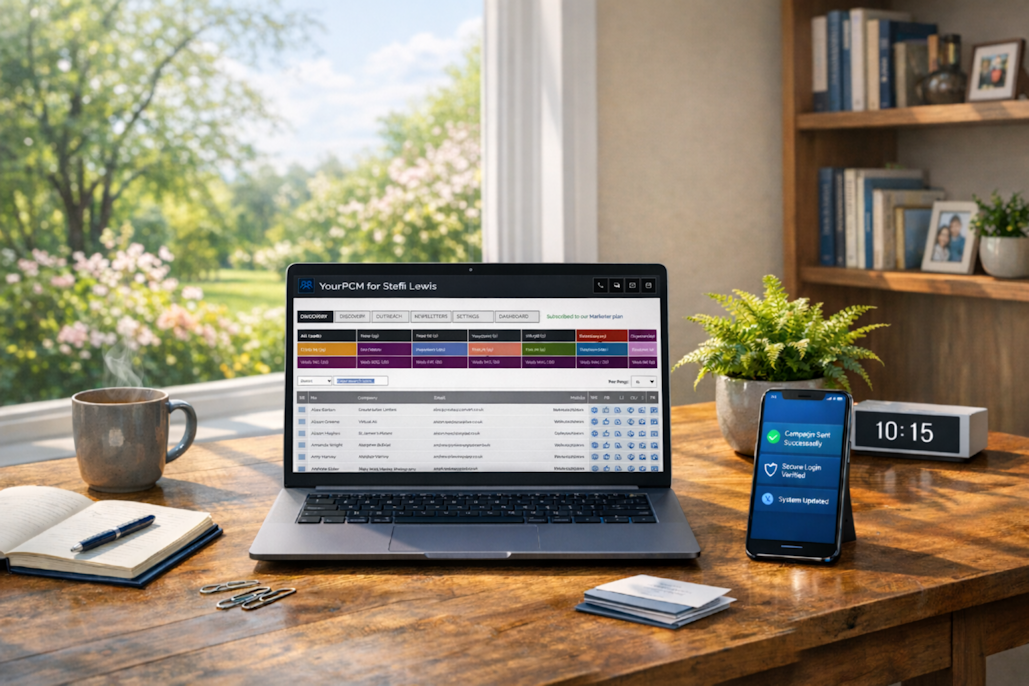 | YourPCM V3: A smart, small business CRM, built for growth Posted by Your PCM on https://www.yourpcm.uk Running a small business means wearing too many hats and having too little time. Your systems should reduce friction, not create it. That's exactly wh ... | |
 | Building A Bookkeeping Business: Increasing Your Prices Posted by Alison Mead on https://blog.siliconbullet.com You may have already done the difficult part of starting your own bookkeeping business; you've found clients, you've decided on your pricing, and now ... | |
 | Companies House says presenter requirements are now delayed until November Posted by Roger Eddowes on https://blog.essendonaccounts.co.uk Companies House presenter requirements have slipped from Spring to November 2026. That gives directors, PSCs, and company agents more breathing space ... | |
 | Moving to Milton Keynes: how Short Stay : MK makes relocation simple Posted by Emily Freeman on https://blog.shortstay-mk.co.uk Moving to Milton Keynes can feel like a lot, especially while you're job-starting and house-hunting at the same time. Short Stay : MK gives you a prac ... | |


